How to Configure Windows Server Firewall

Introduction
Firewalls are a critical component of securing modern networks with internet access. Without firewalls in place, malicious actors could easily access and infect devices on a network. Properly configured firewalls substantially reduce undesirable communications. This article focuses on how to configure Windows Server Firewall.
This article explains how to create firewall rules using the Windows Firewall with Advanced Security console and Windows PowerShell on Windows Server 2016 / 2019 / 2022. Mastering the configuration of the Windows Server Firewall is essential for robust network security.
What is a Firewall?
A firewall controls the flow of data packets in and out of a network. It acts like a barrier, similar to how a physical firewall prevents the spread of fire between compartments. The firewall allows or blocks connections according to configured firewall rules.
Computers behind a firewall cannot receive data until it passes the filters. This greatly enhances security and reduces unauthorized access risks. Benefits of firewalls:
- Prevents unauthorized network access.
- Protects against malware and intrusion attempts.
- Enables secure remote access through VPNs.
- Provides a central point for security policy enforcement.
- Logs network traffic for auditing and analysis.
How Windows Server 2016 / 2019 / 2022 Firewalls Work
The Windows firewall acts as a barrier between local network devices and external networks. When a connection is attempted to a server, the firewall intercepts the traffic and evaluates it against the defined rules.
Only network packets that match the configured rules are allowed through. For example, a rule could allow TCP traffic on port 80 while blocking other ports. Carefully configured rules optimize security while allowing desired connections.
Windows provides inbound rules to control incoming traffic and outbound rules to filter outgoing traffic. Rules can be tailored for each network profile.
Windows Firewall with Advanced Security
Windows Firewall with Advanced Security provides the management interface for configuring Windows firewall settings. It comes built-in to Windows Server without needing additional licensing or hardware. This is a vital tool for how to configure Windows Server Firewall.
There are three default firewall profiles:
- Domain: Applied when the server is connected to a domain network.
- Private: Applied when the server is connected to a private network, like a home or small business network.
- Public: Applied when the server is connected to a public network, like a coffee shop Wi-Fi.
Profiles allow custom rules per network type. You can enable, disable, or configure profiles independently.
Accessing the Firewall Console
To open the Windows Firewall with Advanced Security console:
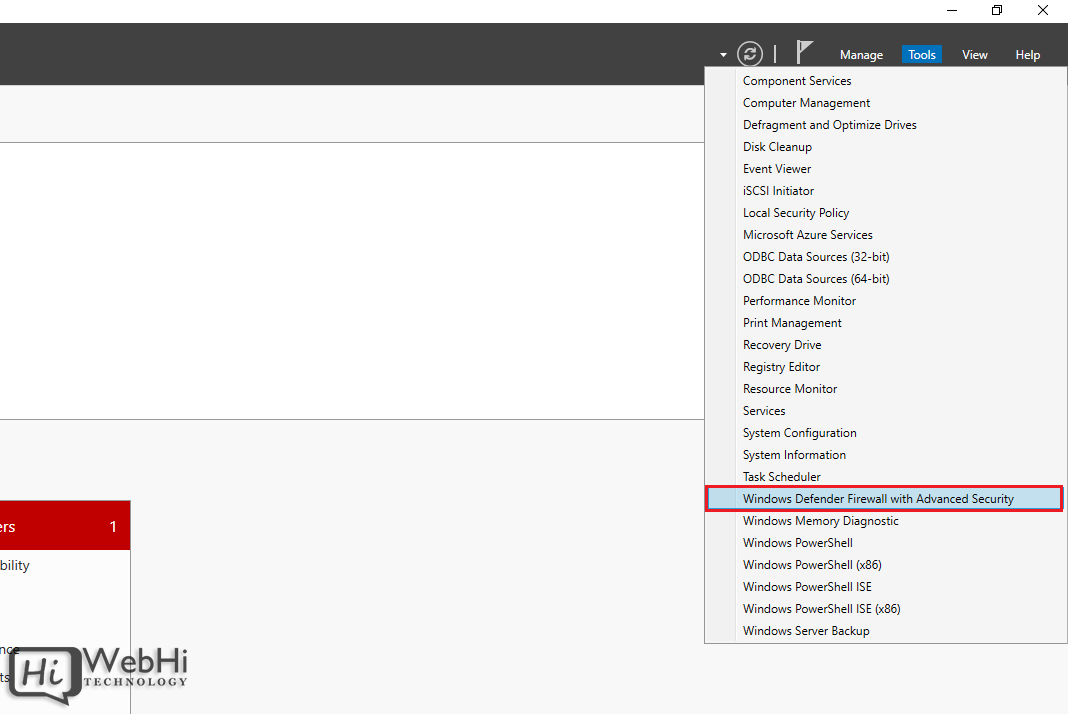
- Open the Start Menu.
- Type "Windows Firewall with Advanced Security".
- Select the result.
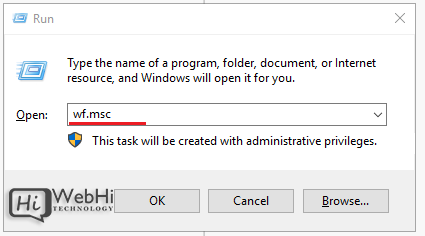
Alternatively:
- Open the Run dialog (Windows Key + R).
- Type
wf.msc. - Press Enter.
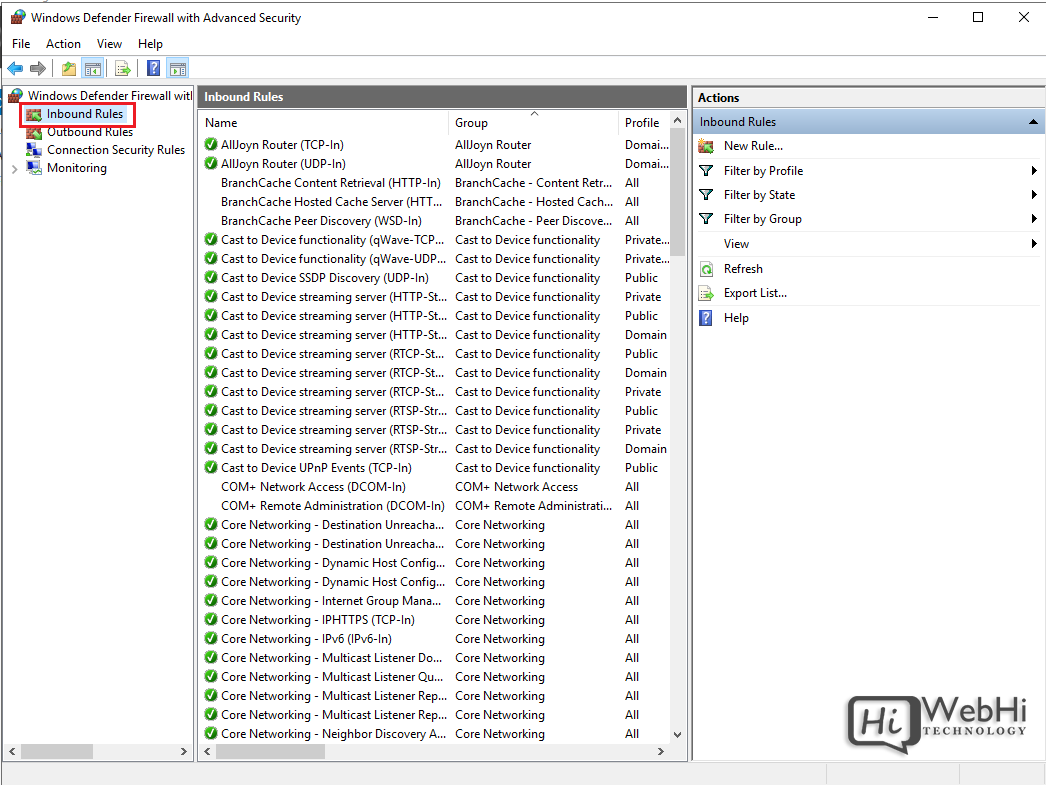
The left menu allows configuring inbound rules, outbound rules, connection security, and monitoring.
Configuring Firewall Rules
Firewall rules control whether to allow or block specific network connections. Rules can filter by:
- Program path
- Port number (TCP or UDP)
- IP address (source or destination)
- Network profile (Domain, Private, Public)
Follow these steps to create an inbound firewall rule:
1. Open the Firewall console and select Inbound Rules
2. Click New Rule to launch the rule wizard
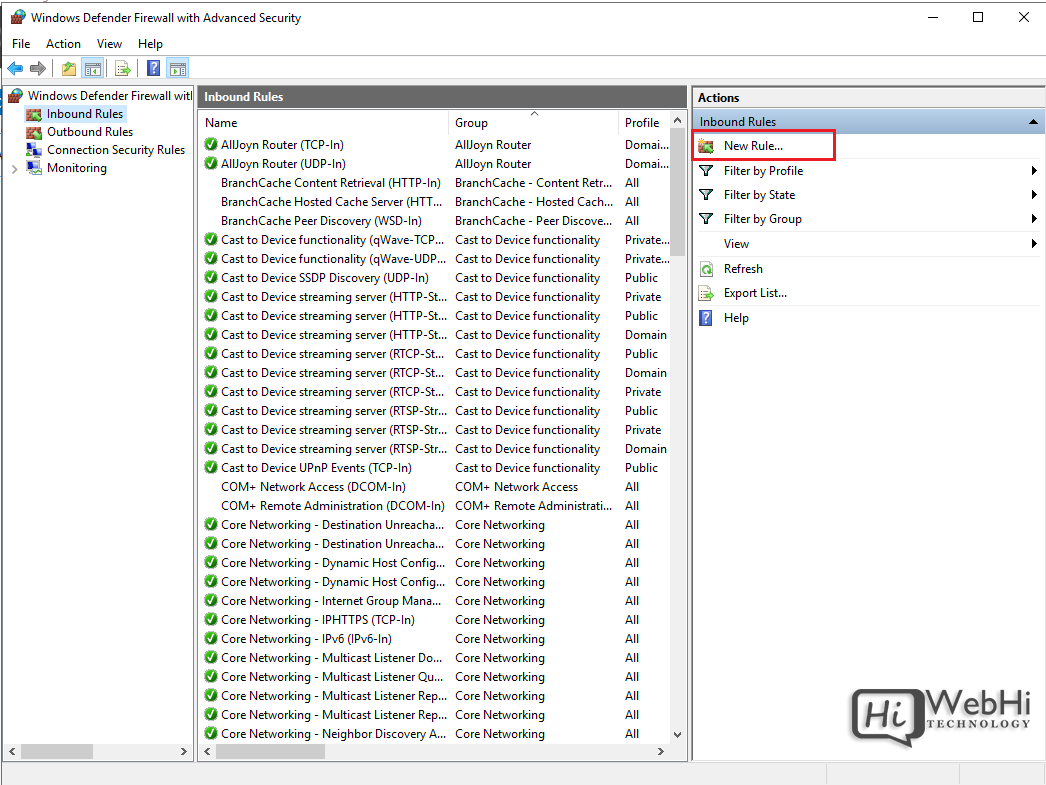
3. Select the rule type – Program, Port, Predefined, or Custom
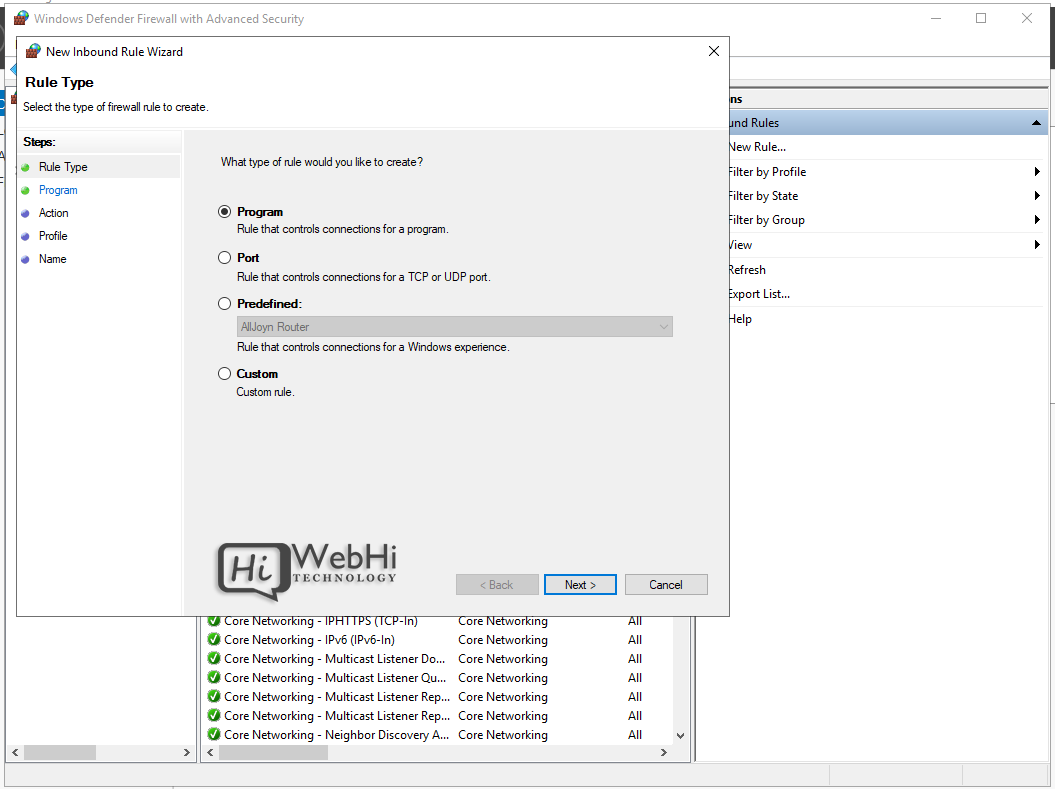
4. Choose All Programs or a Program path
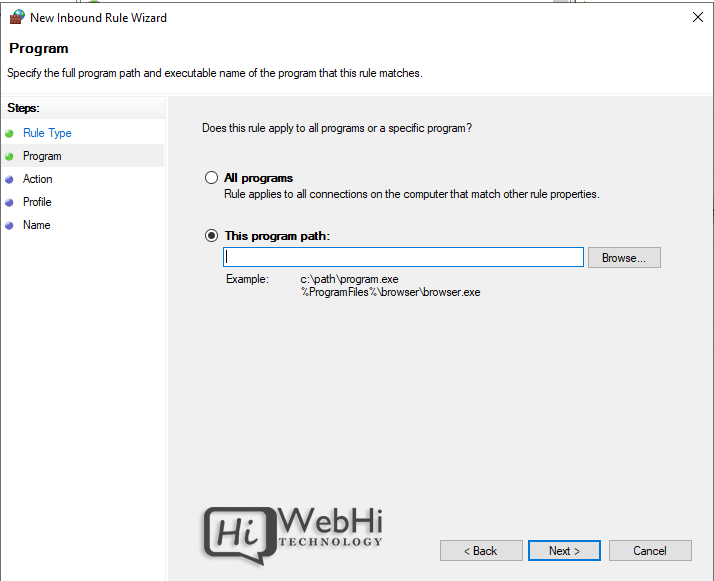
5. Choose Action (allow or block) or allow if connection is secured
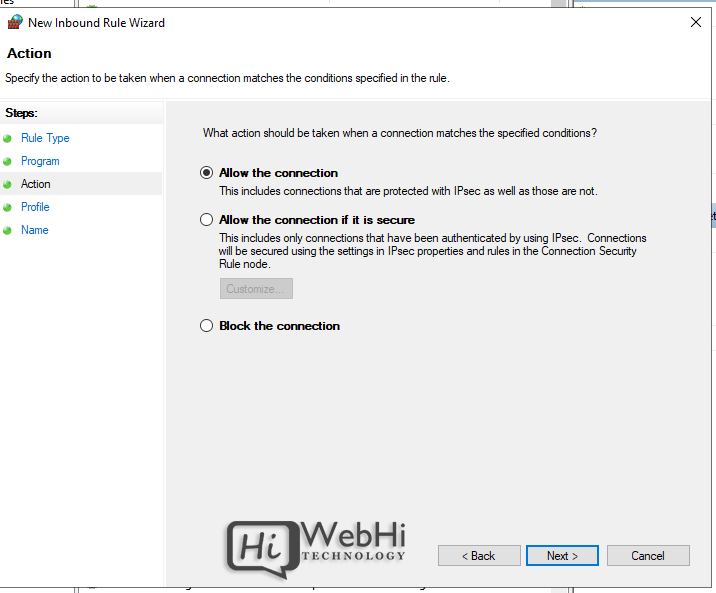
6. Choose profiles
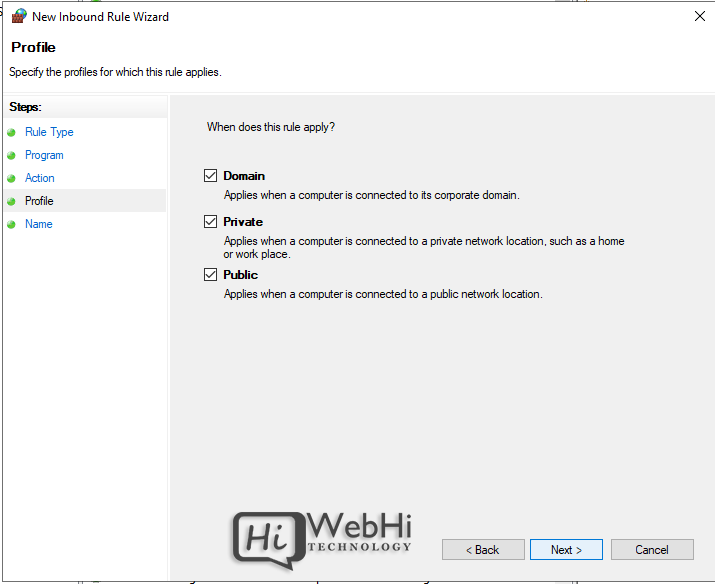
7. Name the rule and click Finish
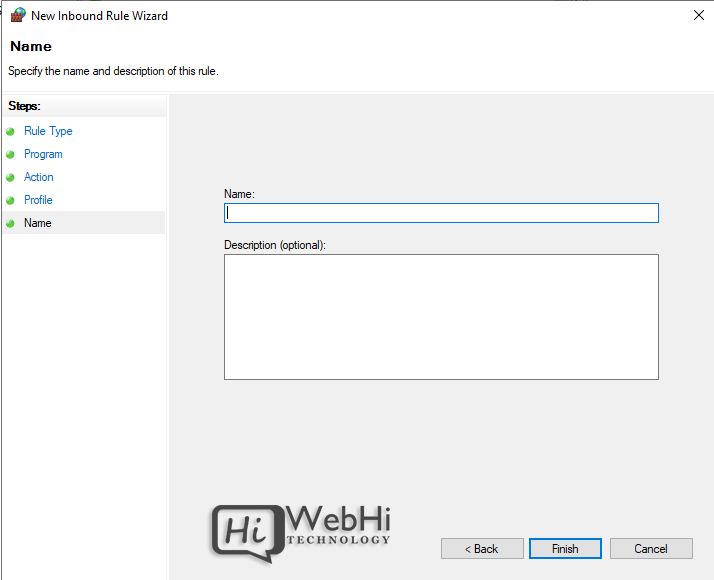
Repeat the wizard for outbound rules. Once created, rules can be edited or disabled from the console.
Rules can also be created from PowerShell. For example:
PS C:UsersAdministrator> New-NetFirewallRule -DisplayName "Allow SSH" -Enabled True -Direction Inbound -Action Allow -Protocol TCP -LocalPort 22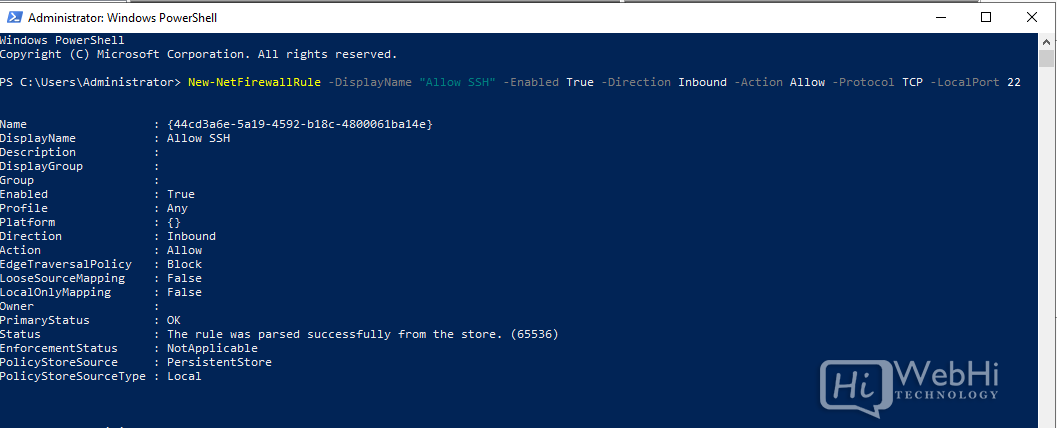
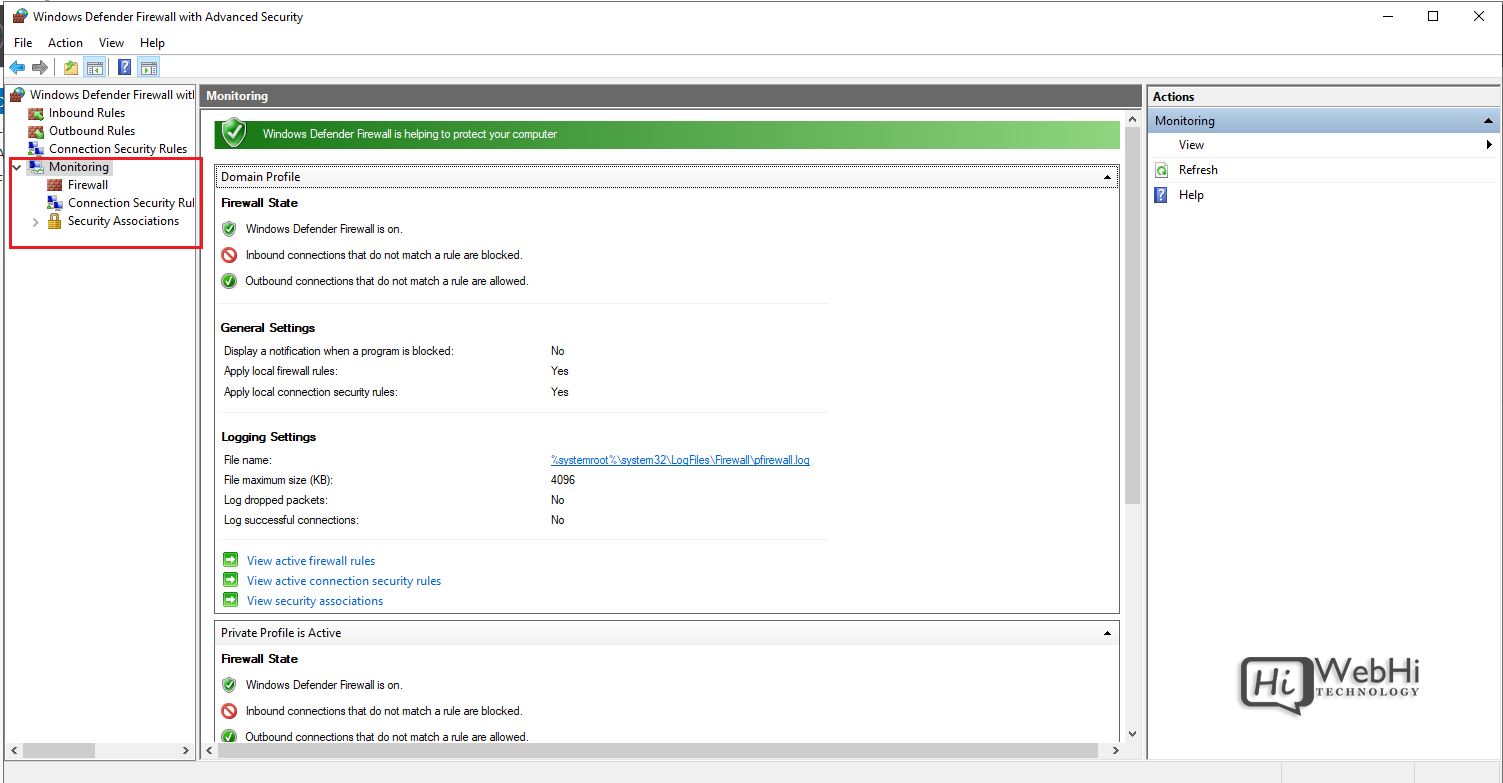
Monitor active connections under the Monitoring tab.
Conclusion
The Windows Firewall provides a flexible and granular rule-based firewall solution for Windows Server 2016, 2019 and 2022. The advanced interface allows creating detailed rules to filter incoming and outgoing traffic as needed. Monitor activity to verify your rules are working correctly. Careful configuration enhances security while allowing desired connections. Understanding how to configure Windows Server Firewall is critical for server administration.
Alternative Solutions for Configuring Windows Server Firewall
While the Windows Firewall with Advanced Security console and PowerShell offer robust control, alternative approaches can simplify management or integrate with broader security strategies. Here are two alternatives:
1. Group Policy Management
For environments with Active Directory, Group Policy Objects (GPOs) provide a centralized method for configuring and deploying firewall rules across multiple servers. This approach ensures consistent firewall policies and reduces the administrative overhead of configuring each server individually.
Explanation:
Instead of configuring the firewall on each server, you create a GPO that defines the desired firewall rules. This GPO is then linked to an Organizational Unit (OU) containing the servers you want to manage. The servers automatically apply the firewall settings defined in the GPO. This significantly simplifies management, especially in large deployments. Furthermore, GPOs offer version control and rollback capabilities, which are beneficial in managing complex firewall configurations.
Steps:
- Open Group Policy Management Console (GPMC).
- Create a new GPO or edit an existing one.
- Navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Windows Firewall with Advanced Security.
- Configure the inbound and outbound rules as needed.
- Link the GPO to the OU containing the target servers.
- Force a Group Policy update on the servers (using
gpupdate /forcein the command prompt) to apply the new settings immediately.
Advantages:
- Centralized management: Configure firewall rules in one place and apply them to multiple servers.
- Consistency: Ensure that all servers have the same firewall configuration.
- Simplified administration: Reduce the administrative overhead of managing firewalls.
- Version control: GPOs provide version control and rollback capabilities.
2. Third-Party Firewall Management Tools
Several third-party firewall management tools offer enhanced features, such as centralized logging, intrusion detection, and automated policy enforcement. These tools can simplify firewall management and provide a more comprehensive security solution.
Explanation:
Third-party tools often provide a more user-friendly interface and additional features compared to the native Windows Firewall. They can also integrate with other security tools, such as SIEM (Security Information and Event Management) systems, to provide a holistic view of the network’s security posture. Some tools also offer advanced features such as application control, which allows you to control which applications can access the network.
Example (Brief):
SolarWinds Firewall Security Manager is a popular example. It allows you to centrally manage firewall rules, monitor firewall logs, and generate reports. Other options include ManageEngine Firewall Analyzer and AlgoSec. While providing code examples for these tools is not feasible within this context due to their proprietary nature, researching their specific documentation will provide information on their APIs and configuration methods. Most integrate via agents installed on the Windows Servers.
Advantages:
- Enhanced features: Third-party tools often offer features not available in the native Windows Firewall, such as intrusion detection and application control.
- Centralized logging: Aggregate firewall logs from multiple servers into a single location for easier analysis.
- Automated policy enforcement: Automatically enforce firewall policies across the network.
- Integration with other security tools: Integrate with other security tools to provide a more comprehensive security solution.
Choosing the right approach depends on the size and complexity of your environment, as well as your specific security requirements. While the built-in Windows Firewall is sufficient for many small to medium-sized businesses, larger organizations may benefit from the centralized management and enhanced features of GPOs or third-party tools. Regardless of the method chosen, properly configuring the Windows Server Firewall is essential for maintaining a secure network.