Install and Secure PhpMyAdmin on Ubuntu 18.04/20.04/22.04 LTS or Debian

Introduction
While many users appreciate the functionality of a database management system like MySQL, they might find interacting with it solely through the command line client less than ideal. For a more intuitive, visual experience, a web interface is invaluable.
PhpMyAdmin was developed to provide this user-friendly interaction with MySQL via a web browser. This guide will walk you through the process to Install and Secure PhpMyAdmin on Ubuntu 18.04/20.04/22.04 LTS or Debian, allowing you to manage your databases on your Ubuntu system securely and efficiently.
Basic requirements
Before diving into the installation, ensure you have the following:
- An Ubuntu 18.04, 20.04, or 22.04 LTS or Debian server.
- A running MySQL or MariaDB database server.
- Apache web server installed and configured.
- A non-root user with sudo privileges.
- A domain name configured with SSL/TLS certificate. This is very important to encrypt traffic.
Finally, there are essential security issues to be aware of when utilizing software like PhpMyAdmin because it is a web-based interface to your database.
For these reasons, as well as the fact that PhpMyAdmin is a widely deployed PHP application that is routinely targeted for attack, you should never execute it on remote computers through a plain HTTP connection. If you do not already have a domain established with an SSL/TLS certificate, you may use this method to create one, securing Apache with Let’s Encrypt on Ubuntu.
Once you’ve completed these steps, you’re prepared to start this guide to Install and Secure PhpMyAdmin on Ubuntu 18.04/20.04/22.04 LTS or Debian.
Step 1: PhpMyAdmin Installation
To begin, we will install PhpMyAdmin from the distro default repository.
$ sudo apt update$ sudo apt install phpmyadmin php-mbstring php-zip php-gd php-json php-curlOn Ubuntu, when requested, you should choose <kbd>apache2</kbd>.
The installation procedure places the phpMyAdmin Apache configuration file in the <kbd>/etc/apache2/conf-enabled/</kbd> directory, where it is immediately read. To finish setting Apache and PHP to interact with phpMyAdmin, the next task in this section of this guide is to explicitly activate the <kbd>mbstring</kbd> PHP extension, which you can achieve by typing:
$ sudo phpenmod mbstringRestart Apache:
$ sudo systemctl restart apache2With that, our phpMyAdmin installation is complete. In your web browser, navigate to your server’s domain name or public IP address followed by <kbd>/phpMyAdmin</kbd>:
http://server_IP/phpMyAdmin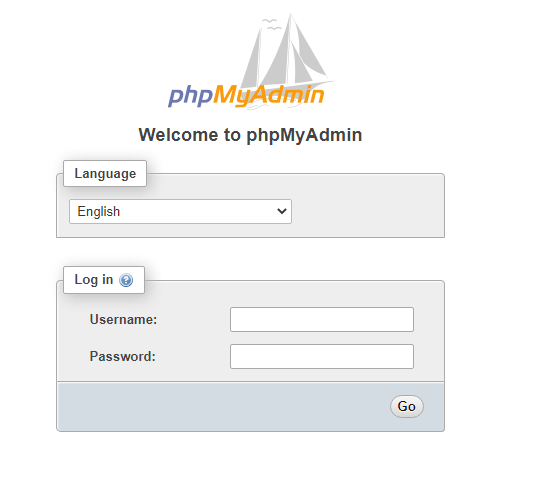
Log in to the interface as root or using another username and password.
Step 2: Secure your phpMyAdmin Instance
At this point, the phpMyAdmin instance installed on our server should be fully functional. We have, however, exposed our MySQL system to the outside world by adding a web interface. Let’s add some layers of security.
Changing the Application’s Access URL
One of the first lines of defense is to change the default URL used to access phpMyAdmin. This makes it less obvious to potential attackers.
$ sudo nano /etc/apache2/conf-available/phpmyadmin.confToward the top of the file, you will see two lines that look like this:
Alias /phpMyAdmin /usr/share/phpMyAdmin
Alias /phpmyadmin /usr/share/phpMyAdminThese two lines are our aliases, which means that whenever we access our site’s domain name or IP address, followed by either <kbd>/phpMyAdmin</kbd> or <kbd>/phpmyadmin</kbd>, we will be sent the content at <kbd>/usr/share/phpMyAdmin</kbd>.
To apply our desired modifications, we should delete or comment out the existing lines and replace them with our own:
# Alias /phpMyAdmin /usr/share/phpMyAdmin
# Alias /phpmyadmin /usr/share/phpMyAdmin
Alias <mark>/secretpage</mark> /usr/share/phpMyAdminTo implement the changes, restart the web service:
$ sudo systemctl restart apache2If you go back to the former location of your phpMyAdmin installation, you will get the 404 error.
Your phpMyAdmin interface, on the other hand, will be available at the new site we chose:
http://server_IP/secretpageSetting up an Authentication to the Web Server :
The next feature we want for our installation was an authentication prompt that a user would have to pass before they could access the phpMyAdmin login screen. This adds an extra layer of security before even reaching the phpMyAdmin login.
Open your config file and add <kbd>AllowOverride All</kbd> in <kbd><Directory /usr/share/phpmyadmin></kbd>
Ubuntu: <kbd>/etc/apache2/conf-available/phpmyadmin.conf</kbd>
<Directory /usr/share/phpmyadmin>
Options SymLinksIfOwnerMatch
DirectoryIndex index.php
AllowOverride All
. . .
</Directory>And Restart Apache
Now that you’ve enabled the use of.htaccess files for your application, you’ll need to make one to create security rules in place.
Create the file in PhpMyAdmin folder:
$ sudo nano /usr/share/phpmyadmin/.htaccessAdd the following lines:
AuthType Basic
AuthName "Restricted Files"
AuthUserFile /etc/phpmyadmin/.htpasswd
Require valid-userSave and close the file when you’re finished.
You chose <kbd>/etc/phpmyadmin/.htpasswd</kbd> as the location for your password file. You can now use the <kbd>htpasswd</kbd> software to create this file and assign it an initial user:
$ sudo htpasswd -c /etc/phpmyadmin/.htpasswd usernamethen enter and confirm a password for the user you are creating.
If you wish to add another user, use the following syntax without the -c flag:
$ sudo htpasswd /etc/phpmyadmin/.htpasswd newuserThen restart Apache to enable <kbd>.htaccess</kbd> authentication.
When you enter your phpMyAdmin subdirectory, you will be prompted for the newly established account name and password:
http://server_IP/secretpage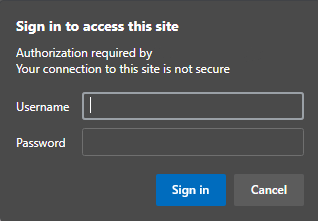
Alternative Solutions for Secure PhpMyAdmin Installation
While the previous steps provide a good baseline for securing your PhpMyAdmin installation, here are two alternative approaches you can consider:
1. Using a Firewall
A firewall acts as a barrier between your server and the outside world, controlling network traffic based on predefined rules. Configuring a firewall like ufw (Uncomplicated Firewall) can restrict access to PhpMyAdmin only to specific IP addresses or networks. This is especially useful if you only need to access PhpMyAdmin from a known location.
Implementation:
First, enable ufw if it’s not already enabled:
sudo ufw enableNext, allow SSH access (if you haven’t already) to avoid locking yourself out:
sudo ufw allow sshThen, allow access to PhpMyAdmin only from a specific IP address (replace your_ip_address with your actual IP):
sudo ufw allow from your_ip_address to any port 80
sudo ufw allow from your_ip_address to any port 443If you need to allow access from an entire network, you can use CIDR notation:
sudo ufw allow from 192.168.1.0/24 to any port 80
sudo ufw allow from 192.168.1.0/24 to any port 443Finally, deny access from all other IP addresses:
sudo ufw default deny incomingReload the firewall to apply the changes:
sudo ufw reloadExplanation:
This method ensures that only traffic originating from the specified IP address(es) or network(s) can access PhpMyAdmin. All other traffic is blocked by the firewall, significantly reducing the attack surface. The ports 80 and 443 are used because the webserver runs on those ports.
2. Using a VPN (Virtual Private Network)
A VPN creates a secure, encrypted tunnel between your device and the server. By requiring users to connect to a VPN before accessing PhpMyAdmin, you add a strong layer of authentication and encryption. This is particularly useful when accessing PhpMyAdmin from multiple, potentially untrusted networks.
Implementation:
There are various VPN solutions available, such as OpenVPN, WireGuard, and commercial VPN services. Here’s a basic example using OpenVPN:
- Install OpenVPN and Easy RSA:
sudo apt update
sudo apt install openvpn easy-rsa- Configure Easy RSA:
make-cadir ~/openvpn-ca
cd ~/openvpn-ca
./easyrsa init-pki
./easyrsa build-ca nopass
./easyrsa gen-dh- Generate Server Certificate and Key:
./easyrsa build-server-full server nopass- Generate Client Certificates and Keys (for each user):
./easyrsa build-client-full client1 nopass- Copy Necessary Files:
sudo cp ~/openvpn-ca/pki/ca.crt /etc/openvpn
sudo cp ~/openvpn-ca/pki/dh.pem /etc/openvpn
sudo cp ~/openvpn-ca/pki/issued/server.crt /etc/openvpn
sudo cp ~/openvpn-ca/pki/private/server.key /etc/openvpn
sudo cp ~/openvpn-ca/pki/private/client1.key /home/youruser/
sudo cp ~/openvpn-ca/pki/issued/client1.crt /home/youruser/- Configure OpenVPN Server:
Create /etc/openvpn/server.conf with the following content (adjust IP addresses and subnet as needed):
port 1194
proto udp
dev tun
ca ca.crt
cert server.crt
key server.key # This file should be kept secret
dh dh.pem
server 10.8.0.0 255.255.255.0
ifconfig-pool-persist ipp.txt
push "redirect-gateway def1 bypass-dhcp"
push "dhcp-option DNS 8.8.8.8"
push "dhcp-option DNS 8.8.4.4"
keepalive 10 120
cipher AES-256-CBC
user nobody
group nogroup
persist-key
persist-tun
status openvpn-status.log
verb 3- Enable IP Forwarding:
sudo nano /etc/sysctl.confAdd net.ipv4.ip_forward=1 and save the file. Then run:
sudo sysctl -p- Configure Firewall (NAT):
sudo ufw allow 1194/udp
sudo ufw route allow in on eth0 out on tun0
sudo ufw route allow in on tun0 out on eth0
sudo ufw enable- Start OpenVPN Service:
sudo systemctl start openvpn@server
sudo systemctl enable openvpn@server- Configure OpenVPN Client:
Create a.ovpnfile on the client machine using the certificate and key.
Explanation:
With a VPN, all traffic between your client and server is encrypted. Accessing PhpMyAdmin requires a valid VPN connection, adding a very strong layer of security, particularly if the VPN uses strong encryption protocols and strong authentication. Only users with valid VPN credentials can access the PhpMyAdmin interface.
Install and Secure PhpMyAdmin on Ubuntu 18.04/20.04/22.04 LTS or Debian is a crucial task for database administrators.
Conclusion
Install and Secure PhpMyAdmin on Ubuntu 18.04/20.04/22.04 LTS or Debian is now complete. PhpMyAdmin should now be installed and ready to use on your server. You may use this interface to create databases, users, and tables, as well as execute standard operations such as deleting and altering structures and data. Remember that securing your PhpMyAdmin installation is an ongoing process. Regularly update PhpMyAdmin, monitor logs for suspicious activity, and consider implementing additional security measures based on your specific needs and risk tolerance.